In this post we will take a closer look at what exactly are denial of service (DoS) attacks, their different types and tools used to perform them. In the recent years, DoS attacks have simply grown from mere annoyances to more serious and high-profile threats to business and e-commerce websites. This is the type of attack that the hackers have successfully used to temporarily bring down major online providers like Yahoo!, eBay and other big players. So, having a clear understanding of the DoS attacks and their working principle seems highly essential for anyone who needs to excel in the field of ethical hacking.
WHAT IS DENIAL OF SERVICE (DOS) ATTACK?
A denial of service (DoS) attack is an attempt to make a system, service or network completely unusable to its intended users or significantly slow down its performance by overloading its resources.
In most cases, if an attacker is unable to gain unauthorized access to the target system he finally decides to carry out a DoS attack by trying to crash its resources. The aftermath of the DoS attack can lead to financial losses especially if the affected website or server is associated with e-commerce activities. It may also affect the goodwill of the company or organization that has become a victim of the attack as there is a clear chance of people losing trust in using its services.
Objectives of DoS Attacks
The objective of a DoS attack is not to gain unauthorized access to the system but rather to prevent the legitimate users of its service from accessing it. To accomplish this, an attacker may use different means such as:
· Attempt
to flood the traffic to the target network so as to make it unreachable
to its intended users.
· Attempt
to disrupt connections between two machines on the network which may
lead to denial of service.
·
Attempt to prevent a particular individual from accessing
the service or disrupt only a specific service from getting accessed.
DoS Attack Techniques
The following are some of the common techniques employed in denial of service attack:
1. Smurf Attack (ICMP flood)
In this type of DoS attack, the attacker broadcasts a large amount of Internet Control Message Protocol (ICMP) echo request packets to a computer network with a spoofed IP address of the target host (victim). This will flood the target host with lots of ping replies (ICMP echo replies) from the network which makes it impossible to handle. There is also a variant of smurf attack called fraggle attack where UDP packets are used instead of ICMP packets. The following figure illustrates the mechanism of a smurf attack:
 |
| Mechanism Of Smurf Attack |
2. Ping of Death (POD)
In this kind of attack, the attacker deliberately sends an IP packet larger than the allowed size of 65,535 bytes. Since the size exceeds the maximum allowed limit, it is split across multiple IP packets known as fragments and sent to the target host. However, when the target tries to reassemble the packet on its end, the fragments add up to more than the allowed size of 65,535 bytes. Being unable to handle oversized packets, the operating system will freeze, reboot or simply crash thereby causing all the services running on it to become unavailable to the legitimate users.
In this way, the attacker becomes successful in causing a denial of service using the ping of death technique.
3. Teardrop Attack
Teardrop attack involves sending IP fragments with oversized payload and overlapping offset value especially in the second or later fragment. If the receiving operating system is unable to aggregate the packets accordingly, it can lead to system crash.
4. SYN Flood Attack
The SYN flood attack exploits a known weakness in the TCP connection sequence called the “three-way handshake”. According to this, a host sends SYN Request to the target server which responds with a SYN-ACK back to the host. Finally the requesting host sends an ACK Response back to the server which completes the three-way handshake process to establish the connection.
However, in case of a SYN attack, a large number bogus TCP SYN requests are sent to the target server but the SYN-ACK response sent back from the server is not answered.
Sometimes the attacker may even use a spoofed IP address while sending a SYN request.
 |
| SYN flood attack |
Now, let us look at some of the popular tools used for DoS attacks.
1. Slowloris
Slowloris is a tool built for Linux platform that targets hosts running web servers such as Apache, dhttpd, Tomcat and GoAhead. This tool works by sending too many HTTP headers to the target server but never completes it. Slowloris is designed to take down a target web server from a single machine by holding as many connections to it as possible.
This will eventually overflow the maximum connections that the target web server can handle thereby leading to a denial of service for other legitimate connections.
2. QSlowloris
This tool works on the same principle as that of Slowloris but has a graphical user interface for ease of use and works on Windows platform.
3. PyLoris
PyLoris is basically a testing tool for servers but can also be used to perform DoS attacks. It can target various protocols including HTTP, FTP, SMTP, IMAP and Telnet.
4. LOIC (Low Orbit Ion Cannon)
LOIC is an open-source network stress testing and DoS tool. It floods the target server with a large amount of TCP or UDP packets resulting in a denial of service.
DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACK
A distributed denial of service attack happens when the attack on the target host originates from multiple compromised systems. Before launching the attack, the attacker compromises multiple systems from one or more networks using trojans and other techniques. These compromised systems are known as zombies where the attacker uses them to launch a DDoS attack on the final target.
The advantages of distributed denial of service is that since multiple systems are used, the target can easily be flooded with too much traffic eventually causing it to go down. A more clear understanding can be obtained using the following figure which illustrates the mechanism involved in a typical DDoS attack.
 |
| DDoS Mechanism |
Characteristics of DDoS Attack
· When
compared to a DoS attack, DDoS is a large scale coordinated attack on the
target using large number of pre-compromised systems (zombies).
· DDoS
attack works under two levels. The final target which is under direct attack is
known as the “primary victim” while the zombies used to attack it are referred
to as “secondary victims”.
· As
the attack originates from multiple network locations and involves large number
of zombies, it is often hard to detect or prevent.
· A
simple DoS attack which originates from a single IP address can easily be
blocked at the firewall level. But a DDoS attack which originates from twenty
to thirty thousand different systems (IP addresses) is extremely hard to
detect.
· Even
if the company makes a guess work and manages to block multiple IP addresses at
its firewall, there is a clear chance of real users being adversely affected as
it is hard to differentiate between genuine and malicious traffic.
DDoS Attack Mechanism
Now let us look at some of the DDoS attack models that are commonly in place:
Agent Handler Model
Agent handler model is one of the popular DDoS mechanisms where the attacker cleverly designs the attack in a hierarchical manner so as to improve its effectiveness and also make it hard to detect and trace back.
 |
| Agent Handler Model |
So, during the time of attack, the attacker cleverly sits at the top of the hierarchy controlling the handlers which in turn initiate the agents (zombies) to attack the target host (victim). Since the attacker safely hides in the background, this type of attack makes it really hard to trace back to the source.
IRC Based Model
IRC based model is similar to the above discussed “agent handler model” but the only difference is that, the attacker makes use of an “Internet Relay Chat (IRC) network” instead of handlers to connect to the agents.
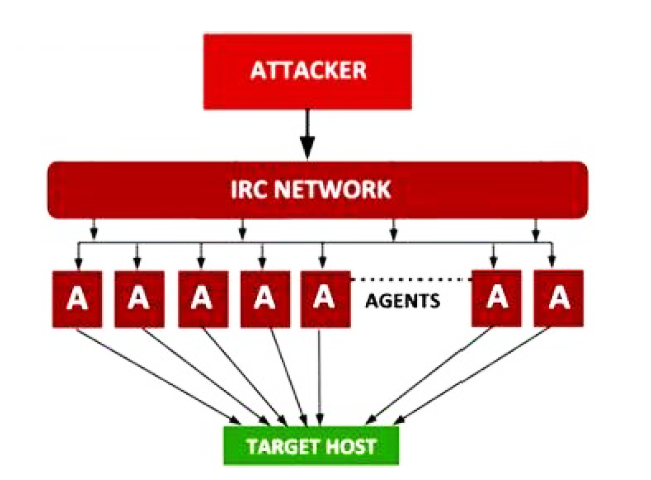 |
| IRC Based Model |
The advantage of this model is that the attacker can use legitimate IRC port to easily connect himself to agents and initiate the attack. Also, huge amount of traffic on IRC network makes it difficult for the network administrator to trace the presence of attacker on the server.
Tools for DDoS Attacks
The following are some of the popular tools used in performing DDoS attacks:
1. Trinoo
Trinoo is a popular tool for DDoS attacks that has a record of taking down large sites like Yahoo! It is designed to cause coordinated DDoS attacks on the target from different locations. This tool basically uses the “remote buffer overrun” vulnerability of systems to get installed and later use them as zombies.
2. DDoSim
DDoSim also known as Layer 7 DDoS simulator is an excellent tool to carry out DDoS attack on the target by simulating several zombies. These zombies create full TCP connection to the target using random IP addresses. It can also perform HTTP based DDoS attacks with both valid and invalid requests.
3. Tor’s Hammer
This is another nice DDoS tool written in Python. It is a highly effective tool that has the capability to take down machines running Apache and IIS servers in a very short time.
The advantage of this tool is that it has the ability to run through a TOR network (anonymous network) to keep the whole attack unidentified.
4. Davoset
Davoset is yet another impressive tool for performing DDoS attacks. It makes use of the “abuse of functionality” vulnerability on sites to use them as zombies and cause DDoS attacks on the target.
COUNTERMEASURES
After exploring a fair amount of information about different types DoS attacks, their mechanism and various tools used in performing them, let us now look at some of the countermeasures that one can take to stop or mitigate such attacks from happening on your systems.
· Using
an IDS (Intrusion Detection System) and IPS (Intrusion prevention
System) can be of a great advantage when it comes to detection and prevention
of DoS/DDoS attacks at an early stage.
· Blacklist
IP addresses that are found to be the source of a possible DoS attack. Ingress
Filtering: Make sure that the incoming packets are coming from a valid
source.
· Egress
Filtering: Scan all the outgoing packets for malicious data before they
actually leave the network.
· Since
it is possible to easily spoof the IP address of incoming DDoS packets, there
is a good chance that the packets will not represent a valid source. So,
configure the firewall to drop packets that do not represent a valid source
address.
· Place
a firewall or packet sniffer that filters out all incoming traffic that does
not have an originating IP address.
· Increase
the available bandwidth or resources to prevent the services from going down
quickly during an attack.
· Load
Balancing: Use a multiple server architecture and balance the incoming load
on each server. This can help improve performance as well as mitigate the
effects of DDoS attacks.


0 comments:
Post a Comment