Due to a rapid increase in the number of Internet users in the recent years, malicious hackers have now started to target individual users for their attack. Numerous client side vulnerabilities such as browser flaws and lack of security awareness among the Internet users has made them an easy target for hackers.
Objectives of Hacking Internet Users
Hackers target individual users for a wide variety of reasons as mentioned below:
· For
gaining access to confidential information such as credit cards details, bank
logins, account information etc.
· To
take control of user’s online accounts such as Email, Facebook and other social
network accounts.
· To
earn advertising revenue by forcefully driving users to online advertisements
such as banners and pop-ups.
· To
use individual users for attacking other systems such as causing a DDoS attack.
· Sometimes
even for fun or to show-off talent among the hacker’s community.
The following are some of the popularly used techniques to hack individual users on the Internet:
Session Hijacking (Cookie Hijacking)
Since web pages have no memories, they have to use a means to identify and authenticate individual users accessing web pages. Especially when people are accessing restricted pages or secure area which require password authentication, the website needs a means to remember users individually after their successful logins. For example, when people log into their Facebook account (by entering password), they may access several different pages until they finally sign out. It would be impractical to ask users to re-enter password each time they access a different page.
Session Cookies
So, when a hacker manages to steal the cookies of an active session he may inject them to his browser to gain unauthorized to any online account such as emails, social media accounts and so on. This technique is known as session hijacking (also referred to as cookie hijacking or cookie stealing).
Session Hijacking Demo
Below is a demonstration of typical session hijacking performed on a sample Facebook account. Here the hacker may use different techniques such as cross-site scripting (XSS) or packet sniffing to steal the target user’s session cookies.
Even though Facebook stores several cookies in the browser after successful login, there are only two important cookies that contains authentication data to decide an active session. The names of these two cookies are as follows:
1. c_user
2. xs
In order to hijack an active session, one has to gain access to the contents of the above two cookies. Snapshots of the sample data contained in these two cookies are shown below:
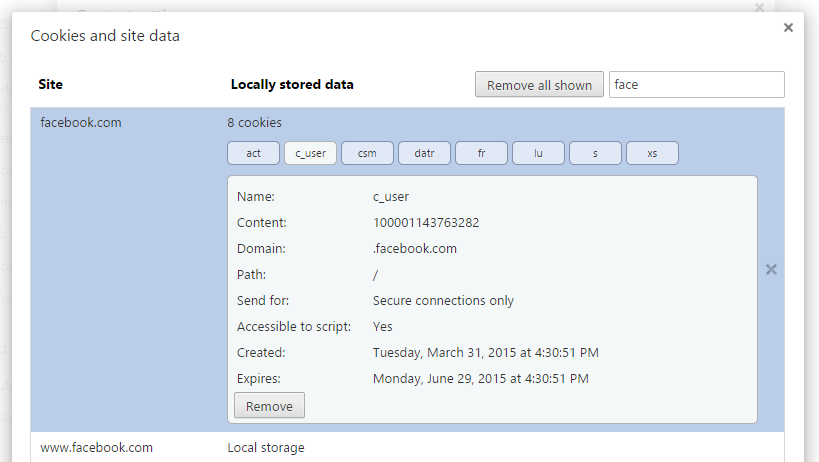 |
| c_user |
 |
| xs |
Once you have access to the contents of the above two session cookies “c_user” and “xs” it is time to inject them to your browser and gain access to the target user’s Facebook account. A Firefox extension called “Advanced Cookie Manager” makes this job a lot simpler. It provides an option to add and edit cookies stored on Firefox. Here is a step-bystep instruction to inject cookie to Firefox browser:
· Install
the add-on Advanced Cookie Manager to your Firefox browser and open it
by clicking the icon present in the toolbar.
· Switch
to the “Manage Cookies” tab and click on the “Add Cookies” button.
· To
create the “c_user” cookie fill in all the details exactly as shown in
the below snapshot expect for the “Value” field which has to be replaced by the
content from the hijacked cookie. Once you are done click on “Add” button.
· Again
click on “Add Cookie” button to create the cookie “xs” in the same way.
After filling the details as shown below click on “Add” button. Do not forget
to replace the “Value” field with the content from your hijacked “xs” cookie:
Once you are logged, you can access the account as long as the target user’s session is active. That means, you can access the account in parallel from your own computer until the user hits “Log Out” button on his/her computer.
Session Hijacking Countermeasures
The following are some of the countermeasures to prevent session hijacking on your computer:
· Use
encryption standards such as SSL (HTTPS) to prevent cookie hijacks via packet
sniffing.
· Use
an up-to-date browser program to prevent browser exploits.
· Configure
browser to stop running unverified scripts and also avoid using browser
plug-ins from untrusted sources.
Email hacking is one of the prevailing hot topics in the field of ethical hacking. A hacker can gain access to a wide variety of private information about the target user if he manager to hack his/her email account. Some of the possible ways to hack email accounts are discussed below.
Keylogging
Using a spyware program such as keylogger is the easiest way to hack an email or any other online account password. All you need to do is just install the keylogger program on the computer where the target user is likely to access his/her email account from. These spyware programs are designed to operate in a total stealth mode and hence remains completely hidden from normal users. Once the keystrokes are recorded you can unlock the program using a hot key combination or password to view the logs. The logs contain all the keystrokes typed on the computer keyboard including the usernames and passwords.
Modern keylogger programs like Realtime-Spy, SpyAgent and SniperSpy supports remote monitoring feature where you can view the logs even from a remote location.
Some of them also have a feature to send logs through email and FTP.
Even though keyloggers can make the hacking process a lot simpler, they have a few drawbacks. Most of these programs have to be installed manually on the target computer for which you need to have physical access to it. Also, there is a chance of anti-spyware programs detecting and deleting the keylogger installation on the computer.
Phishing
Phishing is another popular and highly effective technique used by attackers to hack email and other online accounts. Most Internet users would easily fall prey and become victims to this type of attack. However, to device a phishing attack, one has to have at least a basic knowledge of HTML and programming.
Steps Involved in Phishing Attack:
· The
hacker first creates a replica of the target login page such as Gmail, Yahoo!
Or any other online account.
· This
page is designed to submit all login information (username and password) on the
form fields to a local database instead of the actual website. Hacker would use
a scripting language such as PHP and a database such as MySQL to accomplish
this.
· Once
the page is integrated to the script and database, the hacker uploads the whole
setup to a hosting server so as to make the phishing page go online.
· The
hacker chooses a matching domain (such as gamil.com, gmail-account.com,
yahoo-mail.com etc.) for his phishing page so as to avoid any suspicion.
· Once
the phishing page is live and working, the hacker drives people to this
phishing page by spreading the phishing link via email, Internet Messenger and
forums.
· Since
phishing pages look exactly the same as the real one, people enter their login
details on these pages where they are stolen away and gets stored in the
hacker’s database.
Session Hijacking
As discussed earlier, it is possible to gain access to an email account through session hijacking. By stealing the cookies of an active session and injecting them to one’s own browser, it is possible to gain access to the target email account. However, if the target user closes his/her ongoing session by logging out, you will no longer be able to access the account. Also, unlike keylogging and phishing, this method does not grant you the password of the target account and hence you will not be able to re-access it at a later time.
Unlocking Stored Passwords
Most users prefer to store the password details of email and other online accounts in the browser to enable speedy access. Sometimes login details of offline email clients such as Outlook are also stored on the computer. This makes them vulnerable to hackers. Nirsoft provides a handful of free tools to recover such stored passwords on Windows. You can download the tools from the link provided below:
Download: http://www.nirsoft.net/password_recovery_tools.html
Email Hacking Countermeasures
Below are some of the countermeasures that you can adopt to prevent your email and other online accounts from getting hacked:
· Install
a good antivirus and anti-spyware program on your computer and keep them up-to-date.
· Password
protect your operating system so that no one can access your computer in your
absence.
· Always
perform a malware scan on programs before installing them.
· Avoid
accessing your accounts in public places such as cyber cafes.
· Make
sure that HTTPS is on when you are accessing your emails.
· Do
not click on the links in your email or forum to enter the login page. Instead always
type the URL of the website in the browser’s address bar and also make sure that
HTTPS is enabled on your login page.
· Avoid
storing your login details on the browser unless you are the only user on the computer.
Other Ways to Hack Internet Users
The following are some of the other hacking methods that are common in practice:
· JavaScript:
Since most client-side applications are written in JavaScript,
it also makes a wonderful tool for hackers to write malicious programs for
exploiting browser vulnerabilities. Due to lack of security awareness among
users, they can easily be fooled into entering sensitive information or
navigating to malicious websites. It can also be used to carry out other
attacks such as cross-site scripting and phishing.
· Malware:
Using malware is another popular way of hacking Internet users.
Hackers make use of malware programs like virus and Trojan horses to accomplish
their task by affecting large number of people. A popular example of such
attack is the use of “DNSChanger”
Trojan which affected millions of Internet users by hijacking their DNS
servers.
· Instant
Messaging: Attackers can also target IM users by sending them unsolicited offers
in the form of files and links. This may mislead the users into installing malware
or navigating to malicious websites.




0 comments:
Post a Comment