After gathering a variety of information about the target through footprinting, it is time to move on to the next step called scanning. Scanning is the second step in the intelligence gathering process of a hacker where information about specific IP addresses, operating systems, their architecture and services running on computers can be obtained. Unlike footprinting which gathers information passively from various third party sources, scanning involves actively engaging with the target to obtain information
DETECTING LIVE SYSTEMS
The first step in the process of scanning is to determine whether
the target is alive or not.
This can be done using the ping tool that is readily available on both Windows and Linux computers. Just
open the command prompt if you are on Windows or terminal window if you are on
Linux and type ping followed by the target IP address as shown below:
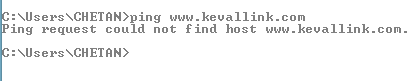
ping www.info-website.net
or
ping 199.79.62.128
If the target is alive and online, you should get a reply from the
target or you if the target is not alive you will get a response saying “ping
request could not find the host www.kevallink.com”.
Angry IP Scanner
You can even ping a range of IP addresses all at once using a nice
tool called “Angry IP Scanner”. It is an open-source cross-platform network
scanner tool packed with several useful features.
All you need to do is enter the starting and the ending IP of the range that you want to ping and click on the “Start”
button as shown in the below figure. This should tell you which of those IPs
are available and which are not.
Angry IP Scanner is available for both Windows and Linux operating
systems and can be
Downloaded from the link below:
Online Ping Tool
If you would like to ping the target using a third party computer
instead of yours, you can do so using online tools like Just-Ping which pings the target from 90 different geo locations worldwide.
You can access Just-Ping tool from the link below:
Just-Ping: http://cloudmonitor.ca.com/en/ping.php
TYPES OF SCANNING
Now,
let us discuss one by one some of the different types of scanning that are in
place.
Port Scanning
Port scanning involves
sending a series of messages to the target computer to discover the types of
network services running on it. Since each service is associated with a “well
known” port number, performing a port scan on the target will reveal the ports
that are open. So, when a port is said to be open the service associated with
it is said to be active and running, thereby opening up the opportunity for the
attacker to break into it.
For
example, if a port scan on the target shows that port 80 and port 25 are open,
that means the target computer has a HTTP service (web server) and an SMTP
service (email service) running on it respectively.
Network Scanning
Network scanning is a
procedure for identifying active hosts on the target network either for the
purpose of attacking them or for security assessment. In this way it would be
possible for the hacker to make a list of vulnerable hosts for direct attack or
to use them indirectly to attack other hosts.
Vulnerability Scanning
Vulnerability scanning involves
the use of automated tools known as vulnerability
scanners to proactively identify security
vulnerabilities of computer systems in a network.
These
tools will scan the target to find out the presence of known flaws that are
susceptible to exploits.
TOOLS FOR SCANNING
The following are some of the popular tools available for
scanning:
Nmap
Nmap is
a popular open-source tool for network discovery and security auditing that
works on different platforms like Linux, Windows and Mac. It basically comes in
the form of a command line interface; however, to facilitate the ease of use it
is also available in a GUI format called Zenmap. For Windows machines, you
can install the “self-installer” version of Nmap that comes in the “.exe”
format. The download link for the same in available below:
Nmap Download: http://nmap.org/download.html
After installing the tool, run the desktop shortcut to open the Zenmap window which typically looks as shown below:
The “Target” box needs to be filled with the target IP address or domain name on which you want to perform the scan. It also comes pre loaded
with 10 different scan profiles that you can select from.
Intense Scan
This scan type should be reasonably quick as it only scans TCP
ports. Additionally, it makes an attempt to detect the OS type, various
services and their version numbers that are running on the target machine.
Intense Scan Plus UDP
It is the same Intense
scan as described above but also
includes scanning of UDP ports.
Intense Scan, all TCP Ports
Unlike the normal Intense scan which only
scans a list of 1000 most common ports, the “Intense scan, all TCP ports”
scans all available 65535 ports.
Intense Scan, No Ping
This option will exclude pinging the target from the Intense scan. You may use this option when you already know that the target is
up or is blocking ping requests.
Ping Scan
This option will only ping the target but does not perform port
scanning of any type.
Quick Scan
Scans faster than the Intense scan by limiting
the number of TCP ports scanned to only the top 100 most common TCP ports.
Quick Scan Plus
Quick scan plus adds OS detection and a bit of version detection features to Quick scan.
Quick Traceroute
This option will show you the route that the packets take to reach
the target starting with the localhost (source or your own computer).
Regular Scan
This will perform the ping and TCP port scan of 1000 default ports
on the target.
Slow Comprehensive Scan
This scan will try all possible options to uncover as
much information as it can about the target. It uses three different protocols:
TCP, UDP and SCTP in order to detect hosts. Out of all the 10 scanning options,
I reckon Intense Scan to be appropriate under most conditions. Just fill the
“Target” box, select the “Intense scan” profile and hit the “Scan” button. Let
us now analyze the Nmap result output by running it on a sample target. After
the scan is completed the “Nmap Output” tab displays the raw output of all the
scan operations such as the date and time it was performed, the
results from ping scan, discovered open ports, target OS and traceroute results as shown below:The other tabs split the same results into an organized manner so as to display them in a more user friendly manner using GUI interface. The “Ports/Hosts” tab will display a list of discovered ports, their status as to whether they are closed or open, the protocol associated and the services running on them. A snapshot of the sample output is shown below:
The “Topology” tab displays the result of traceroute command in a graphical manner showing each hop involved in the path.
The “Host
Details” tab shows the status of the host, its name, number of ports scanned, uptime,
last boot time, type of operating system running including its version number
and many other details as shown in the below figure:
NetScanTools Pro
NetScanTools Pro is
another wonderful program for Windows that has a powerful set of over 50
network tools including both automated and manual ways to retrieve information from
the target.
You can use the “Automated
Tools” to quickly perform port scan and grab vital information about the target
such as DNS records, Whois data, Traceroute details all from a single place. On
the other hand the “Manual Tools” section contains individual tools specially
crafted to give more control in the scanning process for advanced users.
Online Tools
You can also make use of online tools to perform port scan and
discover important information about the target. The following are some of the
links useful online network tools that are worth considering:
PenTest-Tools: https://pentest-tools.com/home
YouGetSignal: http://www.yougetsignal.com/
Other Popular Tools
Here is a list of some of the other popular tools that you may
want to explore:
SuperScan: http://www.mcafee.com/in/downloads/free-tools/superscan.aspx
ipEye: http://www.ntsecurity.nu/toolbox/ipeye/










0 comments:
Post a Comment